Massive Data Compilation: 16 Billion Stolen Passwords
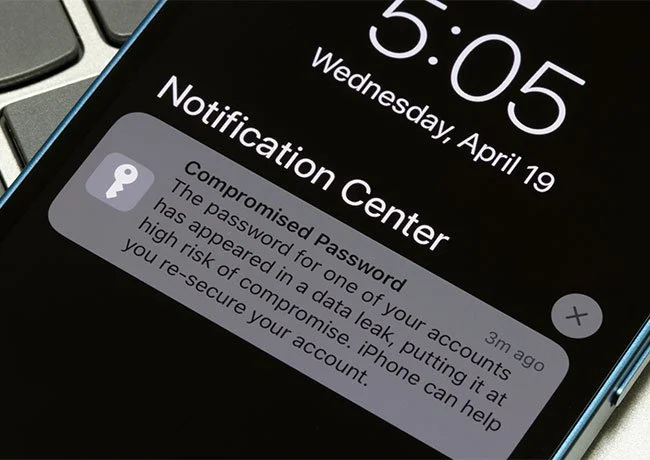
Firstly, a staggering 16 billion login credentials—usernames and passwords—surfaced online. Next, this collection includes data linked to big names like Apple, Google, Facebook, GitHub, VPNs, and even government portals. Then, cybersecurity experts confirmed it’s not one fresh hack. In fact, it comes from dozens of older data leaks and malware infections compiled into one massive trove.
Meanwhile, researchers say this compilation is a blueprint for mass exploitation. Then, cybercriminals can buy the data on the dark web. Next, they can test credentials across multiple accounts to hijack identities, commit fraud, or blackmail victims.
How Real Is the Threat?
First, even though this isn’t a new breach at Apple, Google, or Facebook, users’ accounts are still vulnerable. Next, the scale of this leak makes credential stuffing attacks more likely. Then, those using the same password across services are most at risk .
Moreover, experts highlight infostealer malware as a key driver behind these massive data collections. Additionally, sloppy practices—like storing passwords unencrypted in the cloud—make the problem worse.
Five Smart Steps to Get Safer
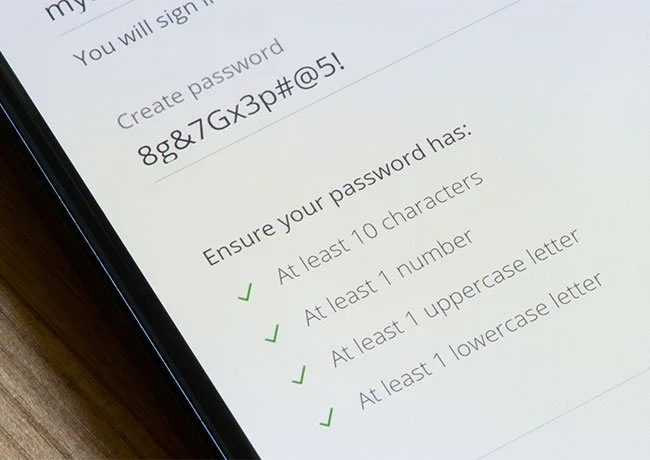
1. Switch to Unique, Strong Passwords
Firstly, using the same password across sites is risky. Next, a single leaked credential can open multiple services. Then, you’ll reduce risk by generating strong, unique passwords—especially with a password manager .
2. Unlock Two‑Factor (or Multi‑Factor) Authentication
Moreover, adding 2FA can block intruders—even if they know your password. First, options include SMS codes, authenticator apps, or physical keys. Then, enabling this extra step significantly ups your account safety .
3. Try Passwordless Options Like Passkeys
Next, companies like Google recommend switching to passkeys. First, these use biometrics or device-based verification. Then, they are harder for hackers to steal or replay than traditional passwords .
4. Keep Software Up to Date
Also, outdated devices and apps often have security holes. First, hackers scan for vulnerabilities in old versions. Then, setting software to auto-update protects against these hidden threats.
5. Monitor the Dark Web for Your Info
Meanwhile, services offering dark-web scans can alert you if your data appears in dumps. First, quick alerts let you respond with updated credentials or extra protections. Then, you regain control fast—before attackers misuse your info.
Why You Should Care Now
Firstly, the breach isn’t hypothetical—it provides exploitable data. Next, attackers can quickly launch credential-stuffing across multiple platforms. Then, anyone using similar login data is at heightened risk.
Moreover, this is more than an abstract warning. First, stolen credentials have been tied to ransomware, phishing, and identity theft. Additionally, these attacks hurt individuals and networks alike .
Then, as data leaks grow more frequent, basic habits become essential. Next, neglecting password health can expose your digital identity—along with banking, email, social media, and professional services.
What Not to Do
Skip using the same password twice. Also, don’t fall for “I’ll remember this one.”
Ignore 2FA alerts—don't. Next, bypassing 2FA via email or SMS weakens its protection.
Delay software updates. Then, you risk known exploits targeting old versions.
Assume no one has your data. Moreover, even old leaks can compromise your current logins.
Routine Maintenance = Fusion of Safety
Daily, Weekly, Monthly Actions
Daily: Use a password manager to auto-fill and check passwords.
When you sign up: Activate 2FA or passkeys right away.
Weekly: Update your primary device, apps, and browser.
Monthly: Run a dark‑web scan. React immediately if credentials appear exposed.
What Companies Should Do
Firstly, organizations need hardened authentication and encrypted storage. Next, they should adopt passwordless login tech. Then, enforcing unique credentials and pushing employees and customers to use MFA helps secure ecosystems.
Moreover, enterprises should conduct frequent phishing simulations and leak-response drills. Also, educating users fosters a stronger, more security-aware culture.
The Takeaway
Ultimately, this isn’t a drill—it’s a clear warning. First, 16 billion compromised credentials are out there. Next, cybercriminals can act quickly unless we take steps to stop them.
Moreover, switching to unique passwords, enabling two‑factor or passwordless logins, keeping apps current, and monitoring leaks offer powerful protection. Then, pairing these habits with strong organizational policies builds real resilience.
In short, responding today can help prevent tomorrow's crisis. Stay alert, stay updated, and stay secure.
Quick Recap
Use a password manager to create unique, strong credentials.
Enable 2FA or use passwordless passkeys.
Keep all devices and apps updated.
Check if your info appears in data dumps.
Adopt safety habits and encourage them around you.